Role of hashing in blockchain
Hashing plays a central role in blockchain technology because it ensures data integrity, immutability, and security. Without hashing, blockchains would not be able to securely link blocks, verify transactions, or generate unique digital identities like wallet addresses.
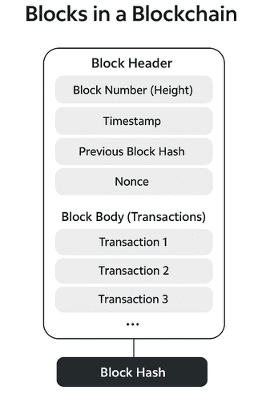
1. Block Linking (Creating the Blockchain)
A blockchain is essentially a chain of blocks, and hashing is what makes this linking secure.
- Each block contains:
- Transaction data
- Timestamp
- Previous block’s hash
- Nonce (used in Proof of Work)
- When a new block is created, all its contents are passed through a hash function (like SHA-256) to generate a unique block hash.
- This block hash is stored inside the next block as the “previous hash.”
Why it matters:
If anyone tries to alter the contents of a block, its hash changes immediately. This breaks the chain since the next block’s “previous hash” will no longer match. Hashing ensures immutability — no block can be changed without altering all subsequent blocks, which is computationally infeasible.
Example:
- Block 100 hash → stored in Block 101’s “previous hash.”
- If Block 100 is tampered, Block 101 becomes invalid.
2. Transaction Verification
Every transaction in blockchain is hashed to ensure security and quick verification.
- A transaction includes details like sender, receiver, and amount.
- This transaction data is hashed and organized in a Merkle Tree structure.
- The Merkle Root (a single hash summarizing all transactions in a block) is stored in the block header.
Why it matters:
- Miners and nodes don’t need to check every transaction one by one; they can use the Merkle Root to verify whether a transaction is valid.
- Even if one transaction is changed, its hash will differ, altering the Merkle Root — revealing tampering.
Example:
Transactions: T1, T2, T3, T4 → Hashes: H1, H2, H3, H4 → H1 + H2 → H12 → H3 + H4 → H34 → H12 + H34 → Merkle Root
This allows fast and secure transaction verification.
3. Address Generation
Wallet addresses in blockchain are also created using hashing algorithms.
- A user generates a public-private key pair using cryptography.
- The public key is passed through a series of hash functions (like SHA-256 followed by RIPEMD-160 in Bitcoin) to generate a shorter, unique wallet address.
Why it matters:
- Addresses protect user privacy — instead of exposing public keys directly, a hashed version (the address) is shared.
- This makes it harder for attackers to derive the original key.
Example (Bitcoin):
- Public Key → SHA-256 → RIPEMD-160 → Bitcoin Address
- Example Address:
1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa(Satoshi’s first Bitcoin address)
Summary
- Block Linking → Each block references the previous block’s hash, ensuring immutability and secure chaining.
- Transaction Verification → Transactions are hashed and structured into Merkle Trees, allowing fast, tamper-proof verification.
- Address Generation → Wallet addresses are derived from hashed public keys, enhancing security and privacy.
In short, hashing is the glue that holds the blockchain together, making it secure, trustless, and immutable.
Continue Learning
Explore more topics in Cryptography in Blockchain or browse other tutorials.